Chapter 2, Protocol Architecture, TCP/IP and Internet-Based Applications.
- You should be able to
- Describe protocol architectures and identify why such architectures are employed.
- Identify the key components of the TCP/IP architecture and briefly describe each.
- Identify the key components of the OSI model and briefly describe each.
- Describe data encapsulation and identify how, why, when this occurs.
- A protocol is a set of rules governing the exchange of data.
- Protocols are normally concerned with three items
- Syntax, or how the data is formatted
- Semantics, or what happens. This includes error handling and control information.
- Timing, or what happens next.
- Architecture is
- look at Websters for a definition.
- What is an ISA from CSCI 312?
- A protocol architecture is a layered structure of hardware and software that supports the
exchange of data between systems. Furthermore this architecture should support distributed applications.
- He starts with an example: File transfer
- Contact must be established
- Something must initiate the communications
- something must be listening to establish this contact with.
- Credentials must be established
- Data about what is to be transfered and how to transfer it must be exchanged.
- The source system must ascertain that the destination system is prepared to receive data.
- Potential data manipulation may need to occur, such as little endian to big endian transfer.
- Something needs to assure that the transfer is complete and complete the session.
- At this level, there is a need to define how to transfer files between machines, that does not involve
- How those machines are connected
- How to break the message into manageable pieces
- How to make sure the pieces get there.
- How to make sure that there are no errors in the pieces
- ....
- A bad programming approach is to put everything into the application, and rewrite it every time you
have a new application.
- A good approach is to build a modular system, or protocol architecture
- These modules are arranged in a stack or layered system.
- Each layer provides a set of services to the layer above.
- Each requests services from the layer below.
- The interface between layers is well defined so that the internals of a layer may change, but the network continues to work.
- The TCP/IP architecture is just such an architecture
- Named for two of the layer protocols that make it up
- TCP - Transmission Control Protocol.
- IP - Internet Protocol
- It came from DARPA
- In general three agents:
- Applications -
- such as mail, ftp
- Concerned with how distributed systems interact and how they exchange data.
- For example, much of the example information is the concern of the application.
- Computers
- Networks
- Originally
- Designed to provide communications across arbitrary, multiple packet switched networks.
- A bad land network
- Packet Radio
- A satellite network.
- It has many configurable parameters because of this.
- The TCP/IP suite has the following layers:
- Physical:
- the actual network hardware
- Characteristics of the media
- What a high signal is
- What the clock rate is.
- Network Access layer
- how the network hardware is used.
- Information such as address of the machine to send the data to, but on the same physical network.
- Quality of service, priority, other network level information.
- This is the local area network, Ethernet, frame relay
- Internet layer
- IP layer
- A router connects two (possibly) different networks.
- The Internet layer provides services for the router to determine things such as
- Where should this packet be sent to next.
- Do I need to change the format of the data?
- Should I allow this packet through?
- Routers "speak" IP, they must be able to examine the packets to determine their destination, source and possibly other details.
- Transport Layer
- TCP layer
- Among other things, is responsible for reliable exchange of data.
- Decides which application to deliver the data to
- Application Layer
- A quick trip through a TCP/IP session
- Let us assume the following configuration:
- A node on my cluster needs to transfer data to a node on my Jim Kirk's machine in physics.
- My cluster is connected by a 1GB Ethernet switch via cat 5 cable.
- The head node is also connected to a 100MB Ethernet switch in the department via cat 5 cable.
- The department's switch is connected to the University's main router via fiber optic cables via 1GB Ethernet.
- The router is also connected to a switch in Hendricks hall via 1GB over fiber.
- The switch in Hendricks connects to Dr. Kirk's machine via cat 5.
-
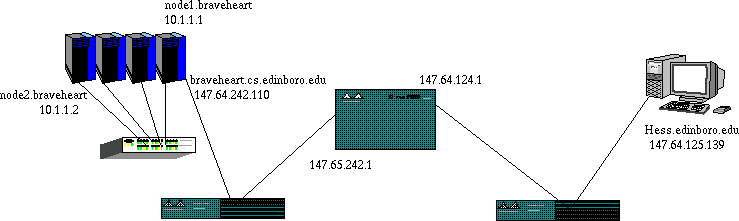
- Notice that there are 3 subnetworks employed in this connection.
- The local network on the cluster
- The LAN for Math and CS
- The LAN for the Hendricks Hall (I assume)
- Each is possibly operating on different media, and employing a different network access protocol.
- In the case of the cluster network
- This is gigabyte Ethernet.
- Each machine has a MAC address (Medium Access Control)
- node 2 is 00:11:11:46:FB:0B, node1 is 00:11:11:4B:31:21
- This address is for the local Ethernet network, is should be unique to each network card.
- Each machine has a unique IP address as well.
- At the Application level, a connection needs to be made between node2 and hess.
- This application will employ TCP ports.
- A port is somewhat akin to a mail box.
- There can be many ports on a single machine.
- Each application needs to be connected to at least one port (assume 54321).
- In the end the source port/ip address destination port/ip address make up a connection.
- The application hands the message, along with the destination ip address and port number to
TCP
- It has already ask TCP to assign it a port on the local machine (12345)
- TCP then deals with the data
- It turns the message into one or more packets.
- It adds TCP header information.
- This includes the source and destination ports
- A sequence number
- checksums plus other information.
- (see page 39)
- This process of adding control information to a packet is called encapsulation
- TCP then hands the data to IP
- Ip then:
- Adds another layer of information to the packet
- Source and destination IP addresses
- Other book keeping information.
- The new datagram is handed to the Network access layer
- The next step is to determine the physical layer address for the packet(s)
- The netmask is or-ed with the destination address and compared to the network
address. (ALL IP)
- If they match, it is for local delivery, so the network access address of the destination is
determined.
- If they do not match, then the network access address of the router is determined.
- This uses one or more routing protocols
- As well as a network access layer protocol such as ARP - address resolution protocol
- The Network access layer
- Once attaches some information such as the MAC address of the router.
- This actually uses both a preamble and a postabmle to generate an Ethernet packet.
- In this case, the mac address will be that of node1
- The packet(s) is/are then placed on the network.
- The switch receives this packet
It examines the destination MAC address and determines to port the
destination machine is headed for.
- It does this by keeping tables of what address it saw on what port last.
- There are all kinds of time to live and other issues at this level.
- It then forms a physical connection between the two ports, and sends the packet on.
- Node 1 receives the packet
- In this case, node 1 is acting as a router.
- It is connecting two dis-similar networks.
- It determines the next step destination via routing protocols in this case, a table lookup.
- It strips off all of the 1GB Ethernet information
- Perhaps it breaks up the packet into more packets (depending on the destination network)
- It then forwards it to the (real I assume) router.
- And the process continues until it reaches Hess.
- On Hess the opposite occurs.
