- A packet switching network accepts packets from a source and delivers them to a destination.
- When it does this it should be
- Correct
- Simple to use
- Robust: Packets should be delivered.
- Things that should not effect the network are:
- Overloads
- Disruption of local service.
- Stability
- Responding to changes can be a problem here.
- Fairness
- Optimality
- Efficiency.
- We need to consider the performance of a routing network
- Easy way: hop count
- More difficult, but perhaps better: Route cost.
- Leads to two routing types: shortest distance and minimal cost.
- If all routes have the same cost, minimum hop count (shortest distance) is minimal cost.
-
- But Sometimes it is not so.
- As we have discussed, delay through the network is another consideration.
- As is throughput.
- Decision time and place
- Before the packet is sent (circuit)
- At each node - distributed
- Central decision
- Centralized anything tends to be easier to implement
- But is more apt to failure
- And is much slower to respond to problems.
- Information:
- What do I have
- Local info only
- Adjacent information
- Some global
- Global
- When do I get it?
- Never
- Occasionally
- Once, at boot time
- At regular periods
- Constantly
- When something changes.
- What do I have
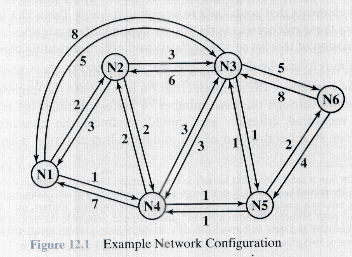
- Table 12.1 summarizes the issues nicely.
-

- Fixed Routing
- Somehow we gain a snapshot of the entire network.
- This must be done when the network is built
- And redone when the network is changed.
- One of the algorithms we are about to discuss are run
- Fixed routing tables are constructed.
- See Figure 12.2.
-
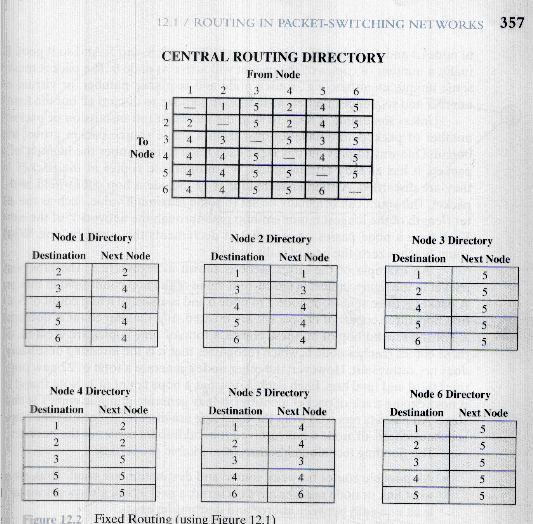
- Stallings notes that in this scheme there is no difference between circuits and datagrams.
- He also notes that that data at each node is just one column of the table.
- This is easy to do
- It can even be done manually.
- But is not at all adaptive.
- Somehow we gain a snapshot of the entire network.
- Flooding
- Can be done completely free of network information.
- The packet sent must include a source, uniq id, destination.
- Note: I made these algorithms up, there are bugs in them
- I assume that each node has a unique ID.
- A simple algorithm
Start: send a packet to each adjacent node: Receive a packet: if source: discard the packet if destination: if the id is new: accept the packet otherwise: discard the packet otherwise: transmit the packet to all adjacent nodes - We can add hop count to make the algorithm somewhat more efficient
Start: send a packet with maximum hop count to each adjacent node: Receive a packet: if source: discard the packet if destination: if the id is new: accept the packet otherwise: discard the packet otherwise: if hop count is 0 discard the packet otherwise decrement the hop count by 1 transmit the packet to all adjacent nodes - An algorithm to discover the a route
on source node: start: for each adjacent edge Send a packet. On any node: on packet receipt: If the packet is a query: If the destination is this node: If this is the first request received Return a route packet with reverse of the path as route otherwise: discard the packet If the source is this node: discard the packet If this node is listed in the path: discard this packet Otherwise: append the source to the path transmit the new packet to all adjacent nodes If the packet is a route: return the packet to previous node in route. - This method will
- Always find the least cost path
- Work as long as there is a route between two nodes.
- Create a Butch of network traffic
- Visit all nodes from the source in a given radius
- It is extremely robust.
- Figure 12.3 takes just a bit of understanding.
- Each packet has the TTL as the data.
- There are two packets on the link from 2 to 1, each with a ttl of 1
- Random
- At any point, select a random adjacent node, send the packet to it.
- Base the probability of selecting a link on the node cost.
- Simple, no network knowledge is needed.
- Adaptive
- We need a network that can respond to
- Failure:
- Someone does something stupid
- Something blows up.
- Congestion
- Failure:
- Problems
- Decision is more complex, thus we need more powerful nodes
- Information is a problem.
- Don't want to kill the network.
- But we do want to respond in time.
- Getting information to the right place at the right time is key.
- We need a network that can respond to