More OS Basics
- Protected Objects
- The os protects a number of things
- Memory
- Shared I/O devices (disks)
- Serially reusable I/O Devices (printers, keyboards, mice, ...)
- Shareable programs and subprocedures
- Networks
- shareable data.
- Some of the protection of these devices is software and some is hardware.
- We need users with different levels of access to appropriately share these resources.
- As some resources have different types of access the granularity of access becomes an issue
- Drives, directories, files, sub-files.
- It is easier to control access to a drive then a record in a file.
- So sometimes the os will need to provide higher level or larger grain access than desired.
- Ie file access vs record access.
- How an OS is designed to protect objects
- We often refer to the central part of an os as the kernel
-

- Generally an OS is constructed of many layers
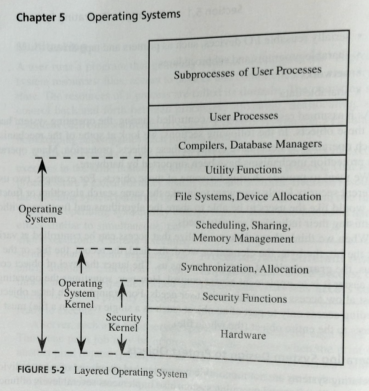
- Each of these has different responsibilities
- Generally the bottom layers are the most security critical.
- Simply because they have greater impact on access to the system.
- The problem is that operations span multiple levels
- Consider passwords, user authentication.
- A user level program may need authentication
- It will rely on a compiler to build this program.
- It will use the system function
getpwnam
- And os functions to open files, access permissions, ...
- And hardware functions for reading, writing, ...
- To make it even more difficult, frequently os has a hook
- Think device driver.
- These are typically supplied by the hardware vendors.
- Windows 10 has an Driver Verifier
- Look at the pink box on that page.
- How the OS is designed for Self-Protection.
- Attacks on the OS can come from all directions
- I thought that this was part of the point of the previous section.
- Programs, drivers, ...
- But the os is the first thing (usually) running on a system.
- They discuss the boot process
- eeprom BIOS to load a boot loader
- Boot loader to load the OS
- Here you can select which os to load
- And how to load the os.
- OS Gradually loads and starts services.
- Unix/Linux can start in single user, network single user, multi user or full mode (and many in between)
- Windows safe mode
- They mention that older hardware had multiple levels of operation.
- But a move towards unlinking hardware from OS meant that this has mostly been abandon.
- Modern hardware needs two modes, user and supervisor.

