More on Threats
- This is chapter 1.2
- In general, cyber experts boil threats down to three basic items
- Availability: the ability of a system to assure that an asset can be used by any authorized parties
- Integrity: the ability of a system to ensure that an asset is modified only by authorized parties.
- Confidentiality: the ability of a system to ensure that an asset is viewed only by authorized parties.
- This is known as the CIA triad
- It is foundational, dating back to the 70's
- Sometimes the following are added:
- Authentication: The ability of a system to confirm the identity of a sender.
- nonrepudiation or Accountability: the ability of a system to confirm that a sender can not convincingly deny having sent something.
- Auditability: the ability of a system to trace all actions related to a given asset.
- Clearly CIA is not everything, but
- It is a strong foundation for thinking about system security.
- How can someone obtaining your password to the MACS system impact CIA?
- In this case concentrate on your homework files, these are your asset.
- What is the value of this asset?
- Confidentially: They now have access to your files, they could submit one as themselves.
- Integrity: They could change your files, a program you intended to submit could be changed so it doesn't work, or compiles with errors, ...
- Availability: They could change your password, or even remove all of your files. You could no longer access your data, or even the system.
- They identify four ways assets can be harmed
- Interception
- Interruption
- Modification
- Fabrication
- They go on to take a closer look at the CIA triad
- Confidentiality
- Obviously you want your records to be confidential.
- But also little bits of information can increase vulnerabilities
- If you are traveling and someone gained access to your GPS data.
- Plus observed that there are no tire tracks in the snow on your driveway.
- And mail is piling up in your mail box.
- They could reasonably assume you are traveling and your home becomes more vulnerable.
- This is not self disclosure
- Posting vacation pictures on facebook increases this vulnerability as well, but that is self inflicted.
- This becomes more difficult when the situation becomes more complex
- Think about your student records
- Who has legitimate access to this data?
- Do they have access to all of the data?
- What if they share this data, even inadvertently?
- Who owns the data?
- Think about class attendance data in terms of the above questions.
- What is the value of class attendance data?
- What are the threats to class attendance data?
- They point out properties that could mean failure of data confidentiality
- An unauthorized person accesses a data item
- An unauthorized process accesses the data.
- A person or process with access to part of the data accesses a part they do not have authorization to access.
- An unauthorized person accesses an approximation of the data
- Example: Learning someones salary range.
- An unauthorized person learns of the existence of new data.
- In all of the above:
- You assume there is some policy which details who should have access to data.
- There is a access mode defining the type of access
- In the end, the confidentially is tied to the ability to read or view data.
- Integrity
- In this section, the book describes integrity much wider than I thought.
- Remember, they previously said The ability of a system to ensure that an asset is modified only by authorized parties
- In this section they propose the definition of integrity includes
- precise
- accurate
- unmodified
- modified only in acceptable ways
- modified only by authorized persons or processes
- consistent
- internally consistent
- meaningful and usable.
- In the end, they stick with the first definition.
- And note that integrity can be maintained only be rigorous control of who can access what data and in what ways.
- All of this should be based on policy.
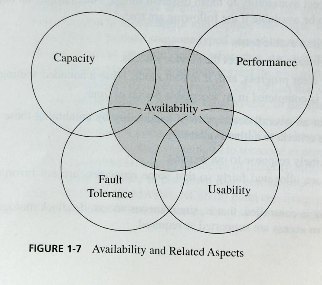
- Availability
- Ransomware
- Note here that availability means
- County buildings closed.
- No visiting hours at the detention center
- No marriage licenses
- Plus they shutdown their servers, so who know what else they can't do.
- The book points out that availability applies to services and data
- Something is available if
- It is present in a usable form
- It has enough capacity to meet the service's needs
- It is making clear progress, and, if in wait mode, it has a bounded waiting time.
- The service is completed in an acceptable period of time.
- Criteria for availability are
- There is a timely response to a request
- Resources are allocated fairly so that some requests are not favored over others.
- Concurrency is controlled; that is simultaneous access, deadlock management, and exclusive access are supported as required.
- The system has the ability to deal with faults.
- The system is easy to use in the way it is intended to be used.
- This is summed up in figure 1-7
- In the end, for data
- Viewing is confidentiality.
- Changing is integrity.
- Using is availability.
- Access Control
- To implement a policy, computer security control all accesses by all subjects to all protected objects in all modes of access.
- Access control can be defined in terms of
- A policy that defines
- Who has what access to which object.
- For example
- In linux we see file permissions
- These will describe who (user, group, others)
- Has access (read, write, execute)
- To what files.
-
- They note
- A small, strong centralized control of access is fundamental to preserving confidentiality and integrity.
- But it probably makes it very difficult in terms of availability.
- It is will create a single point of failure.

