Types of Threats
- They start with a picture from a report in 1970
- Here is the document
- The first 15 or so pages of classification are amusing.
-
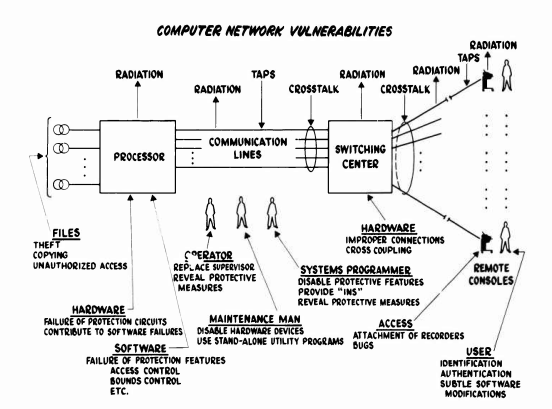
- This details the vulnerabilities of a system 50+ Years ago.
- Or humans who interact with the system.
- Edward Snowden "is an American former computer intelligence consultant who leaked highly classified information from the National Security Agency (NSA) in 2013, when he was an employee and subcontractor." (Wikipedia)
- Chelsea Manning "is a former United States Army soldier who was convicted by court-martial in July 2013 of violations of the Espionage Act and other offenses, after disclosing to WikiLeaks nearly 750,000 classified, or unclassified but sensitive, military and diplomatic documents." (again Wikipedia)
- Human threats can be
- Benign:
- Accidental spilling a drink on a keyboard
- Unintentionally deleting a file.
- Malicious
- Intentionally causing harm.
- This is called an attack
- A random attack is where the attacker just wants to cause harm somewhere.
- A directed attack is the opposite, there is a specific goal for the attack.
- It is often difficult to tell which is occurring until well into, or even after the attack.
- You can't know all of the treats
- There are too many
- People come up with new ones.
- Development (hardware, software, policies, people) constantly introduce new vulnerabilities.
- But they list two sites of interest
- Types of attackers
- Someone playing
- Little or no skill
- Script Kitty
- Breaks systems for the excitement
- But doesn't know what they have.
- The lone hacker
- Breaks systems for the challenge.
- Generally knowledgeable
- Perhaps doesn't even do anything.
- Or could be quite malicious
- An angry/hurt individual
- ex-employee breaks the system for revenge
- APT
- Government Agencies
- Hacktivist
- People who break in to protest.
- Organized Crime
- Up to and including "hacker for hire"
- Terrorists
- This has become evident
- Elements
- Computers are the target of an attack.
- Computers are a tool of attack
- Computers are used to organize attacks (communications, logistics, ...)
- Computers as an enhancer of attack (recruitment, propaganda)
- APT - Advanced Persistent Threat
- Attacks coming from organized, well financed, patient assailant's.
- Think Government sponsored attackers.
- APT
- Long term focused attacks.
- Detailed research on targets (people and systems)
- Including spear phishing
- Silent, skilled, difficult to catch.
- Current News
- There are good stories in the book, read it.
