End of chapter 1
- Harm is the negative consequence of an actualized threat.
- Harm is everything from disclosed information to stolen hardware.
- On page 22 "The number and kinds of threats are practically unlimited because devising an attack requires an active imagination, determination, persistence and time"
- There are many threats
- Natural disasters
- Human errors and mistakes
- Deliberate attack.
- You need to prioritize what you will protect against.
- What you don't protect against is residual risk.
- Risk management consists of deciding what risks to attempt to mitigate.
- This involves the value of the asset
- The likelihood of the threat.
- Attackers generally need three items
- Method: the knowledge, skills and tools to exploit a vulnerability
- Motive: a reason to attack
- Opportunity: the time and access to carry out the attack.
- They define the attack surface as a system's set of all vulnerabilities, actual and potential.
- Finally Controls
- Controls or countermeasures are a means to counter a threat.
- The list the following
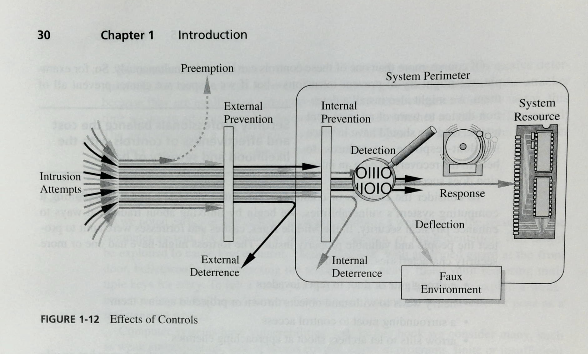
- prevent: block the attack or remove the vulnerability
- deter: make it harder to perform the attack
- deflect: make another target more attractive.
- mitigate: reduce the impact of the threat
- detect:
- recover
- Take a look at figure 1-12 Effects of Controls
- Remember, you are always balancing the cost and effectiveness of the control against the likelihood and severity of harm.
- The tighter you lock up a system:
- The lower the risk of threats
- But the lower the ease of usefulness.
- They list several types of controls
- Physical controls: locks, doors, ...
- Procedural or administrative:
- policies that define how to use the system
- You can't use external cloud storage
- You can not use personal equipment at work.
- Technical controls
- Passwords
- Encryption
- firewalls.