Types of Threats
Objectives
We would like to :
- Understand different threats.
Notes
- This continues Pfleeger chapter 1.
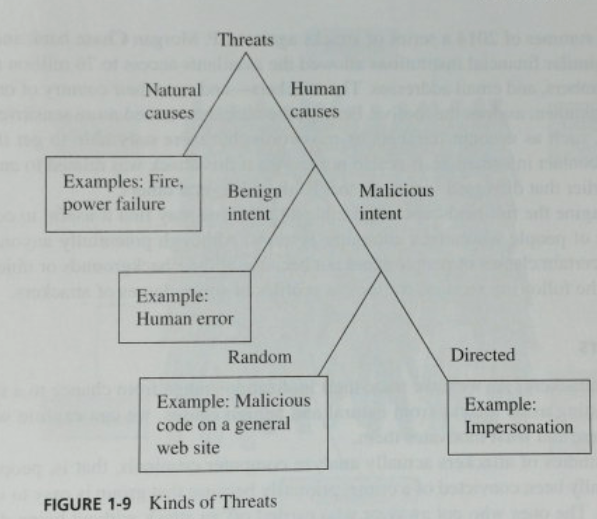
- Remember, a threat is a potential cause of harm to the system.
- It is not the weakness that could be exploited to cause the harm.
- Threats can be human or not.
- (I) A manufacturing defect might cause loss of data
- (A) A natural disaster could cause harm
- Threats can be malicious or not.
- An accident, oversight or other human error could cause a threat.
- (C) An email message sent to the wrong person
- (I) Bad backups when installing a new operating system.
- (A) A dropped hard drive, broken network cable
- In the case of a human caused, malicious or deliberate threat, we frequently use the term attack.
- We break attacks down into two general categories
- Random: most victims are just targets of opportunity
- Tries to get into every computer they find.
- Code posted to a web site hoping someone will download and install it.
- Directed or targeted: where the attacker intends harm to a specific target.
- An attempt to change a grade in a grade book.
- An attempt to gain access to an individual company.
-
 (from Pfleeger)
(from Pfleeger)
- An Advanced Persistent Threat (APT) is a long-term cyberattack where attackers attempt to gain access to a specific target.
- APTs are usually
- Larger organization
- Nation State
- "Criminal" organization
- Well Funded
- Well organized an professional
- Motivated by a long term goal (espionage, disruption)
- Examples
- Stuxnet: The US Government developed software to disrupt Iran's nuclear research/work.
- Fancy Bear: A group, most likely operated by Russia targets NATO aligned states.
- What can we say about the attackers?
- There have been multiple studies and generalizations
- There is an attempt to draw broad categories, and this is useful.
- But attackers might match no pattern or multiple patterns..
- The study is limited to the people we know, by the way
- Self identified
- And those caught.
- It does not include those we don't know! (DUH)
- Broadly we have the following groups
- Individuals
- May be interested in systems and exploring for fun
- May be interested in the challenge, prestige
- Revenge, profit, ...
- Organized groups
- Organized Crime
- Wizard Spider
- Developed ransomware tools
- Hire people who may not know they are working for a criminal organization.
- Professional
- Possibly controls large "networks" of broken computers
- Well resourced and organized.
- Nation States
- Terrorist groups
 (from Pfleeger)
(from Pfleeger)